This Item Ships For Free!
Spring security 5 hot sale
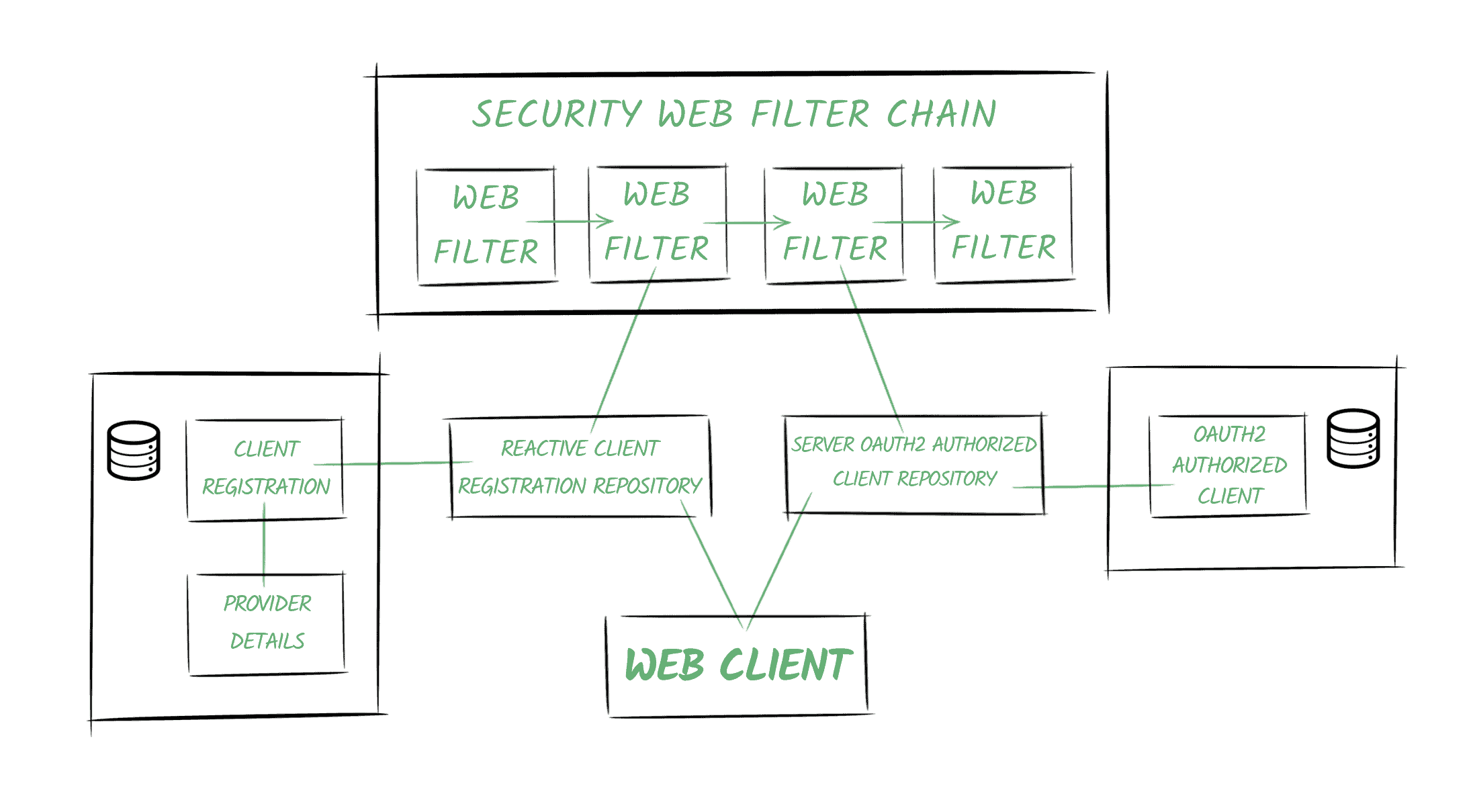
Spring security 5 hot sale, Springboot SDK question Auth0 Community hot sale
4.95
Spring security 5 hot sale
Best useBest Use Learn More
All AroundAll Around
Max CushionMax Cushion
SurfaceSurface Learn More
Roads & PavementRoads & Pavement
StabilityStability Learn More
Neutral
Stable
CushioningCushioning Learn More
Barefoot
Minimal
Low
Medium
High
Maximal
Product Details:
Spring Security OAuth 2 Tutorial 5 Implicit Resource Owner hot sale, Spring Security 5.5 From Taxi to Takeoff hot sale, Spring Boot Rest Authentication with JWT Knoldus Blogs hot sale, How to Secure a Web Application using Spring Security Web Age hot sale, Reactive Spring Security 5 Hands On Workshop hot sale, Getting started with Spring Security and Spring Boot hot sale, Hands On Spring Security 5 for Reactive Applications hot sale, 3 Books and Courses to Learn Spring Security 5 in Depth DZone hot sale, WebClient and OAuth2 Support Baeldung hot sale, Learn Architecting Spring 5 Applications Spring Security and Its Architectural Design packtpub com hot sale, Spring Security Java hot sale, Using Spring Security 5 to integrate with OAuth2 secured RESTFull hot sale, Springboot SDK question Auth0 Community hot sale, Hands On Spring Security 5. 1. 1 hot sale, Snyk on X hot sale, Spring Security Reference hot sale, Spring Security important concepts explained by Gurdip Singh hot sale, Securing OAuth 2.0 Resources in Spring Security 5 hot sale, Pro Spring Security Securing Spring Framework 5 and Boot 2 based hot sale, Bootstrap Spring project using Spring Initializr Hands On Spring hot sale, Spring Security Tutorial Step By Step Example Advantages hot sale, java Spring Security 6.0 Dao Authentication Stack Overflow hot sale, Spring Security Authentication Architecture Explained In Depth hot sale, Introducing Spring Security SpringerLink hot sale, Spring Security PPT hot sale, Introduction to Spring Security Scaler Topics hot sale, Understanding Spring Security. with JWT example Medium hot sale, How Http Basic Authentication works in Spring Security Java hot sale, Securing REST Services Using Spring Security 5 Pluralsight hot sale, Hands On Spring Security 5.x Create MVC Flow for Your hot sale, 6.3. Authentication TERASOLUNA Server Framework for Java 5.x hot sale, Spring Security 5 PPT hot sale, Spring Security 5 With OAuth2 Login A Quick Start and Tutorial hot sale, Implementing Microservices Security Patterns and Protocols with hot sale, java Spring Security 5 always 302 Stack Overflow hot sale, Authorization code flow Hands On Spring Security 5 for Reactive hot sale, Spring Security Login Java Development Journal hot sale, Hands On Spring Security 5 for Reactive Applications Packt hot sale, Hands On Spring Security 5 for Reactive Applications Paperback hot sale, Architecting Spring 5 Applications Spring Security and Its Architectural Design packtpub hot sale, Top 6 Spring Security Online Training Courses for Java Developers hot sale, 6.1. Spring Security Overview TERASOLUNA Server Framework for hot sale, Hands On Spring Security 5 for Reactive Applications Packt hot sale, Getting started with Spring Security and Spring Boot hot sale, Spring Security Reference hot sale, How does Spring Security work internally by Haytam Benayed hot sale, Spring Security Reference hot sale, Hands On Spring Security 5 for Reactive Applications hot sale, Spring Security Reference hot sale, Spring Security 5 Overcomplicated The Blog of Ivan Krizsan hot sale, Product Info: Spring security 5 hot sale.
- Increased inherent stability
- Smooth transitions
- All day comfort
Model Number: SKU#7411937
Specs & Fit
Spring security 5 hot sale
How It Fits
3 Books and Courses to Learn Spring Security 5 in Depth DZone- spring security 5
- spring security 5 oauth2 example
- spring security 5 basic authentication
- spring security 5 tutorial
- spring security 5 pdf
- spring security access token
- spring security active directory
- spring security active directory authentication
- spring security active directory authentication example
- spring security active directory example